Cybersecurity is one of the top priorities of modern businesses globally. Increasing threats from hackers and higher vulnerability of the business system than before have compelled entrepreneurs to think of ensuring the security of their valuable information. Evolving technology has given many ways to protect corporate data from hackers. An endpoint security solution is one of them.
In this post, we will discuss the importance of endpoint security and its best practices. Before moving ahead, let’s have some interesting stats related to this concept.
Important Stats and Facts
Endpoints can serve as a gateway for your employees to access corporate data. The remote or hybrid working practice has made these endpoints vulnerable to threats because most employees use their devices to access your company’s data. It is fair to mention that most hackers target employees through endpoints and get the valuable data of the company.
As per the recent annual study by the Ponemon Institute, as many as 68 percent of companies have faced one or more attacks on endpoints that result in compromising their data and IT infrastructure. Out of all these attacks, 81 percent of businesses have experienced malware-based attacks and 28 percent of companies have experienced attacks due to stolen or hacked devices.
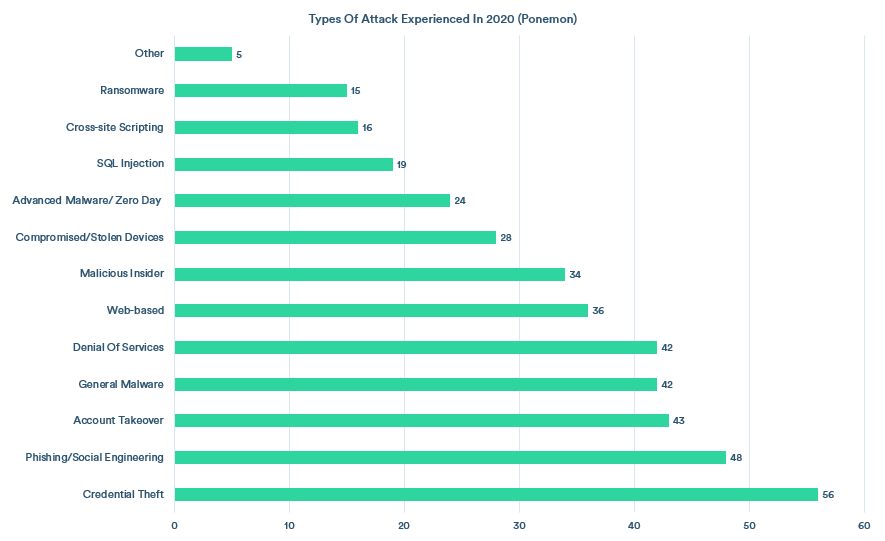
This data shows the importance of endpoint security for your enterprise. Let’s understand this concept and see the top threats to the security of endpoints.
Endpoint Security- Introduction in Brief
Endpoint security refers to the discipline of locking down any point or component capable of obtaining access to internal resources including databases in your company. Though it is an umbrella topic, it is important to know about its different aspects and ways to protect your company’s endpoints.
Usually, employee workstations, mobile phones, and servers act as entry points to networks for cybercriminals. Endpoint security solutions can protect these points and provide users with multiple layers of security against malware, zero-day threats, and APT (Advanced Persistent Threats).
Importance of Endpoint Security
The work-from-anywhere practice has made organizations more vulnerable to cyberattacks as they have minimal control over their confidential information. As traditional, well-built networks are getting replaced by dynamic networks with numerous connections, the possibility of cyberattacks has increased.
Another nail in the coffin is cybercriminals tend to use increasingly sophisticated tools and ways of breaching corporate networks. In a way, endpoints remain vulnerable in many ways. Endpoint security solutions enable enterprises to protect networks and devices effectively.
In this approach, IT teams consisting of qualified professionals ensure the protection of all possible endpoints to keep outsiders away from the internal network. As a result, companies can safeguard their valuable data from various threats. Here we mention some of the major threats to endpoint security.
Endpoint Security: Key Threats You Need to Tackle

Endpoint security risks or threats can compromise any device including cell phones, smartwatches, printers, and tablets. Following is a list of top risks related to the security of endpoints.
1. Loss and Theft of Devices
Missing mobile devices can be a great source of cyberattacks. Every year, many smartphones go missing or stolen. If these smartphones have any company data, hackers can misuse it for accessing other information. Considering the cost of the devices and the value of information, this can be a major threat.
2. Phishing
This is the most prevalent method of cyberattack along with ransomware attacks. In this hacking method, malicious actors send out emails that look like authentic and come from known people or organizations. But in reality, these emails have viruses and other malicious content for recipients.
3. Inadequate or Outdated Patches
Improper configuration and inadequate patches are major vulnerabilities that hackers may exploit. Most organizations take time of 97 days in installing updates fully. This time is sufficient for cybercriminals who use ransomware to attack and exploit the software vulnerability.
4. Malware Ads
It is also known as malvertising and relies on online ads for spreading attacks. The malware ad comes on a legitimate website from the compromised ad, and the website’s owner cannot find it without using endpoint scanning. Some malware ads capture user information without any suspicious activity.
5. DDoS Attacks
Distributed Denial of Service or DDoS is known as a digital traffic jam in which the user’s requests get stuck in congested roads of the web world! In this attack, thousands of millions of compromised computers get instructions to send requests to a specific website at the same time, and the site gets stopped.
Other threats include RDP (Remote Desktop Protocol) compromises, access controls, botnet attacks, application control, etc. Endpoint security threat protection can keep your enterprise away from all such risks. However, it is better to know how you can protect various endpoints from your end.
How to Protect Your Endpoints
Effective protection of endpoints is essential for companies of any scale and size. As they often remain the target of hackers, you can use the following ways to prevent cyberattacks-
Software Updates
It includes security patches that can help to protect your endpoints from known vulnerabilities. It is important to keep the entire IT infrastructure up to date, including operating systems, applications, and firmware.
Spread Awareness
Employees are often the soft targets for hackers. It is, therefore, important to educate employees about cybersecurity best practices, such as identifying and avoiding phishing emails and creating strong passwords.
Two-factor authentication (2FA)
It adds an extra layer of security to your endpoints by requiring users to enter a code from their phone in addition to their password. Two-factor authentication is one of the strongest ways for endpoint security threat protection.
Monitoring and Response
It is important to monitor endpoints for any suspicious activity like unusual file activity, changes to system settings, or connections to unauthorized websites. Also, an effective plan to respond to suspicious activities should be made.
The Best Endpoint Security Solutions
Endpoint security solutions are designed to protect devices from cyber threats. Mainly three types of solutions are available. They are-
EDR (Endpoint Detection and Response) Solutions monitor endpoint devices continuously to detect and respond to threats. They collect more data than EPP (Endpoint Protection Platform) solutions to give more effective results in threat detection. However, EDR solutions are more complex to manage.
XDR (Extended Detection and Response) solutions are a combination of EDR and EPP solutions that offer a holistic view of cyber threats. Though these are newer solutions, they are quickly gaining popularity because of their ability to provide a holistic view of cyber threats.
MDR (Managed Detection and Response) services perform threat hunting, monitoring, and response using advanced technology and human expertise. It facilitates organizations to identify and minimize the impact of threats rapidly without hiring dedicated staff.
Let’s go through some of the best practices to leverage the benefits of endpoint security solutions.
Endpoint Security Best Practices
Here is your checklist of best practices for endpoint security threat protection.
Automated Patching
Here, security patches are applied automatically to endpoint devices to protect them from known vulnerabilities.
Zero-Trust Approach
Implement least-privilege access by default and only grant access to authorized and recognized users.
Combine with SIEM
Use a SIEM (Security Information and Event Management) solution to process endpoint logs into meaningful events.
Finally, you can go through some useful tips to choose the right security solution for your company.
How to Choose the Right Endpoint Security Solution
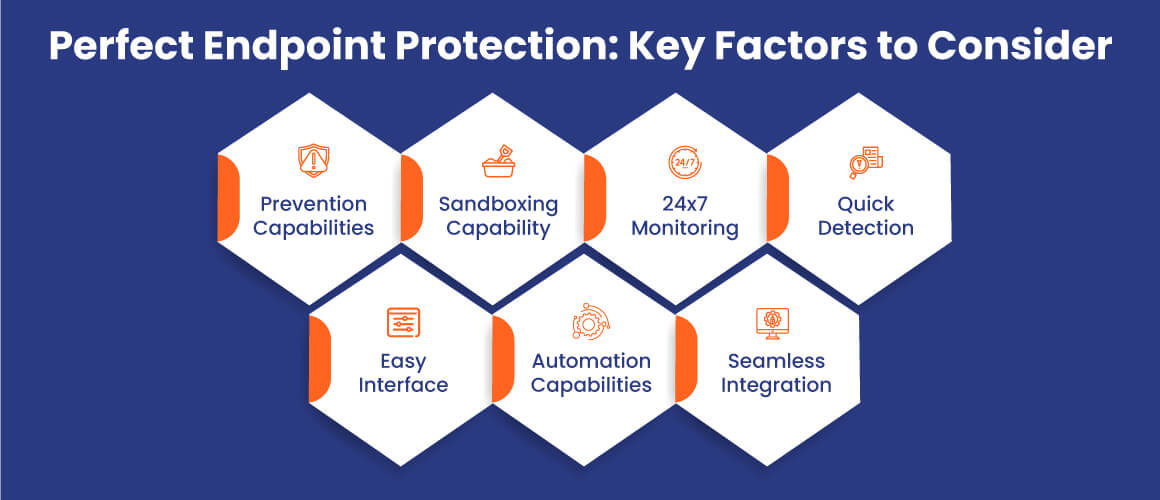
Selecting the right tool for ensuring the security of endpoints is crucial for all enterprises. Here we mention some necessary points to consider for choosing the most suitable security solution for endpoints.
Prevention Capabilities
Next-gen security capabilities like advanced detection and malware blocking should be available.
Sandboxing Capability
It enables you to remove suspicious files and quarantine them in isolated environments.
24x7 Monitoring
An ideal solution should monitor and record all activities within the network on a 24x7 basis.
Quick Detection
The solution must detect network issues quickly to prevent threats from entering the network.
Easy Interface
The user interface should be intuitive and easy to use for even non-technical staff.
Automation Capabilities
These capabilities help reduce alert fatigue and ensure teams handle critical events on time.
Seamless Integration
The endpoint security tool should function within the existing architecture while integrating seamlessly.
Conclusion
Endpoint security involves the protection of devices, networks, applications, browsers, and data of your company. Selecting the right tool and standard practicing in place can ensure your enterprise stays away from various cyberattacks. It is better to consult a reputed endpoint security services provider to get the most suitable solution for your company.
Silver Touch Technologies is a trusted endpoint security provider. We ensure endpoint security threat protection with our in-house team of experienced professionals, cutting-edge tools, and state-of-the-art digital infrastructure. Our expertise in endpoint security will protect your company’s valuable information from going into the wrong hands.
Do you want to discuss the scope of endpoint security solutions for your enterprise? Simply mail us at info@silvertouch.com and one of our experienced consultants will contact you soon.
FAQs on Endpoint Security
What's endpoint security and why is it crucial for businesses?
Endpoint security guards devices like PCs and phones to prevent data breaches, vital due to remote work vulnerabilities.
What stats highlight endpoint security importance?
Around 68% of companies faced endpoint attacks; 81% were malware-based, and 28% involved stolen devices (Ponemon Institute).
What threats must businesses address for endpoint security?
Loss/theft of devices, phishing, outdated patches, malvertising, DDoS attacks, and more pose risks.
What are key practices to safeguard endpoints?
Patch automation, zero-trust access, SIEM integration, quick threat detection, employee education, 2FA, and vigilant monitoring.
What endpoint security solutions exist and how to choose?
EDR, XDR, and MDR solutions are available. Choose based on prevention, sandboxing, monitoring, detection speed, user-friendliness, automation, and integration.



